Last year in March hackers stole sensitive data of millions of Americans from Equifax, one of America's biggest credit reporting agencies. In this massive breach, data including passports credit card numbers, driver's licenses as well as the Social Security numbers of nearly 146 million consumers were stolen.
One of the most significant data scandals in 2018, for sure, was at Facebook in March 2018 when a political data firm called Cambridge Analytica collected sensitive data of 87 million Facebook users. On top, in June 2018 it was revealed that another app called Nametests.com had publicly exposed information of more than 120 million users.
We could name a whole list of data breaches which had significant impacts for the victims and analysts and politicians discussing the lessons learned and how enterprises could have prevented this misery from happening (List of Top 10 of Americas biggest data breaches in 2018). But one area you never hear them talk about is how Enterprise Architecture could assist in the prevention of data breaches.
You can imagine what a data scandal implies for Equifax or Facebook including reputation damage, a loss of profits and legal proceedings. On top, the recent GDPR law, which came into effect in May 2018, will add further penalties to organizations like them.
Having this in mind, the Equifax and Facebook data breach with its subsequent lessons should be worth a discussion of millions of Euros. Consequently, an organization should have a more in-depth look into how Enterprise Architecture may improve the data protection.
The penalties for noncompliance are very steep. Here is the penalty breakdown within the GDPR regulation:
Fine: 10,000,000 Euros or 2% of your company's Global Turnover, for offenses related to:
- Child consent;
- Data processing, security, storage, breach, breach notification;
- Transfers related to appropriate safeguards and binding corporate rules; and
- Transparency of information and communication.
Fine: 20,000,000 Euros or 4% of Global Turnover, for offenses related to:
- Consent;
- Data processing;
- Data subject rights;
- Non-compliance with GDPR order; and
- Transfer of data to a third party.
Data security with enterprise architecture
Data security has always been on the priority list of an organization’s management team. However, the Enterprise Architecture team is rarely involved given the fact that EA is one approach to improve data compliance.
It’s a surprise because when you consider EA use cases and how much of an organization it infuses, EA should have a say in data security planning.
Facebook and Equifax are great examples to explain how EA should be integrated in the data protection and security planning process. These two data breach examples should undoubtedly trigger a re-evaluation of the company’s data security policies, procedures, and technologies.
A solid and lean Enterprise Architecture forms the foundation of data security and consequently helps to mitigate risk in an organization. An EA’s 360-degree view of the organization means security can be involved in the planning stages, decrease risks involved in new implementations. When it comes to security, EA should take the driver's seat!
Furthermore, Enterprise Architecture helps to detect and eliminate threats originating from shadow IT, redundant applications, and other IT missteps. An up-to-date view of the entire Architecture enables an organization to get the best possible view of its current technology assets. In order to assess the software versions that are in use, we recommend using a technology stack to group your software. You can also tag your software (manually or using out-of-the-box LeanIX tags) to reference them in the future. In the screenshot example below, you can see that we have tagged them via the Candidate, Leading, Exception, Sunset model.
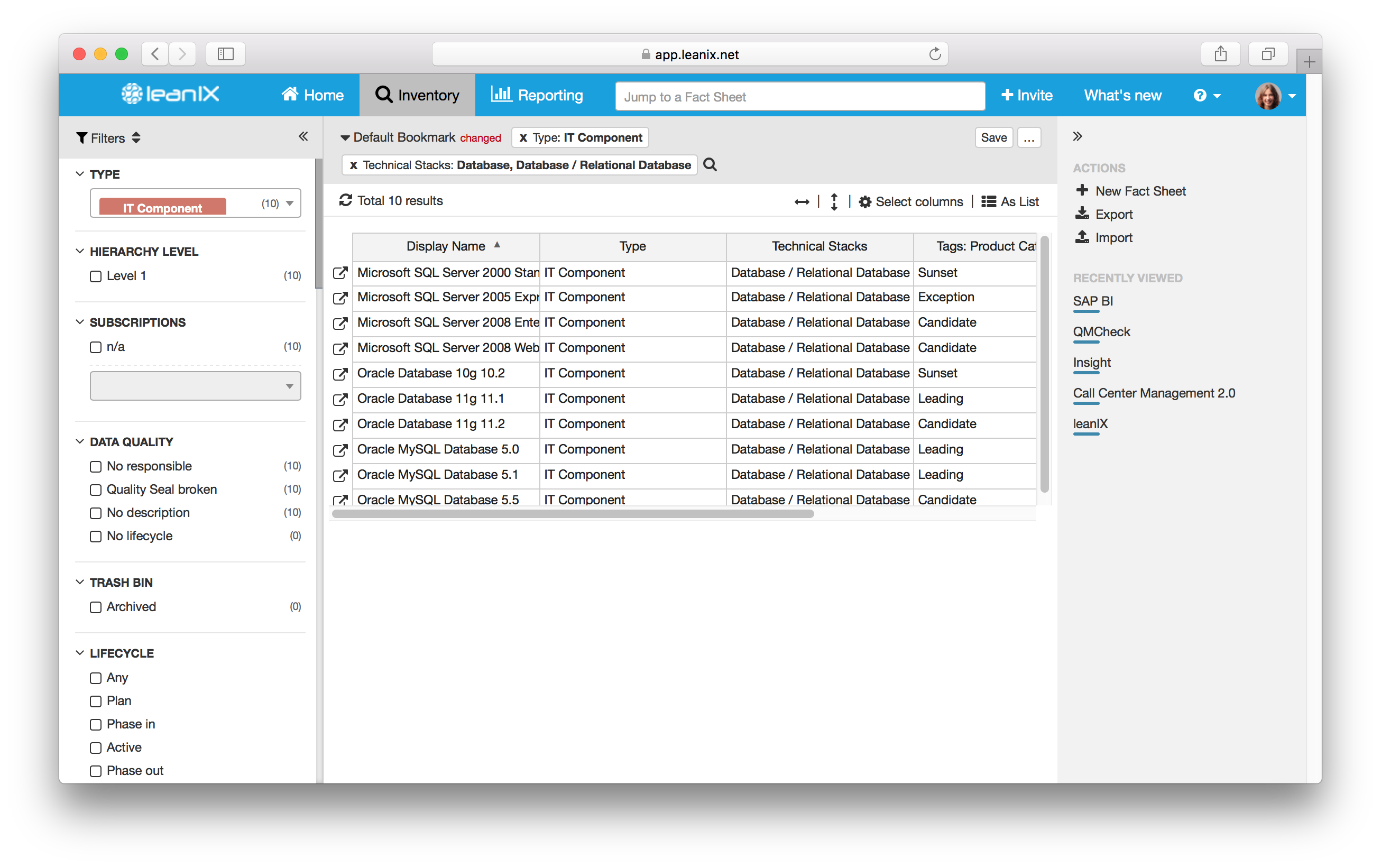 Image 1: List showing which technology stacks are being used and their status.
Image 1: List showing which technology stacks are being used and their status.
In the case of Equifax the breach could have been prevented as it had been attributed to the company’s failure to update a web application although it had sufficient warning to do so.
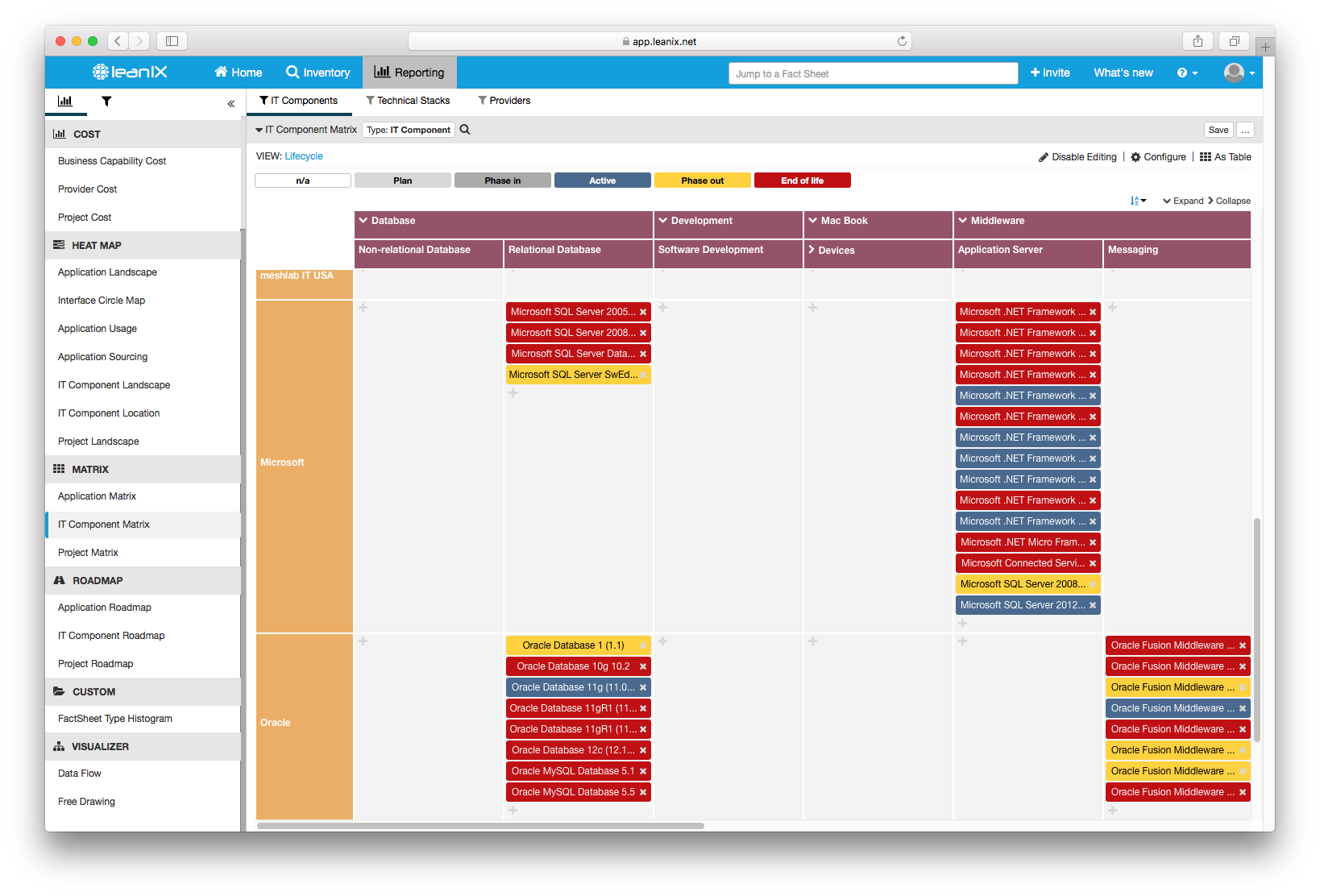
With a lean EA tool like LeanIX applications, which are at risk as the underlying IT components are out of the lifecycle can be viewed in the Application Landscape heat map and redundant IT Components are easily spotted in the IT Component Matrix of LeanIX.
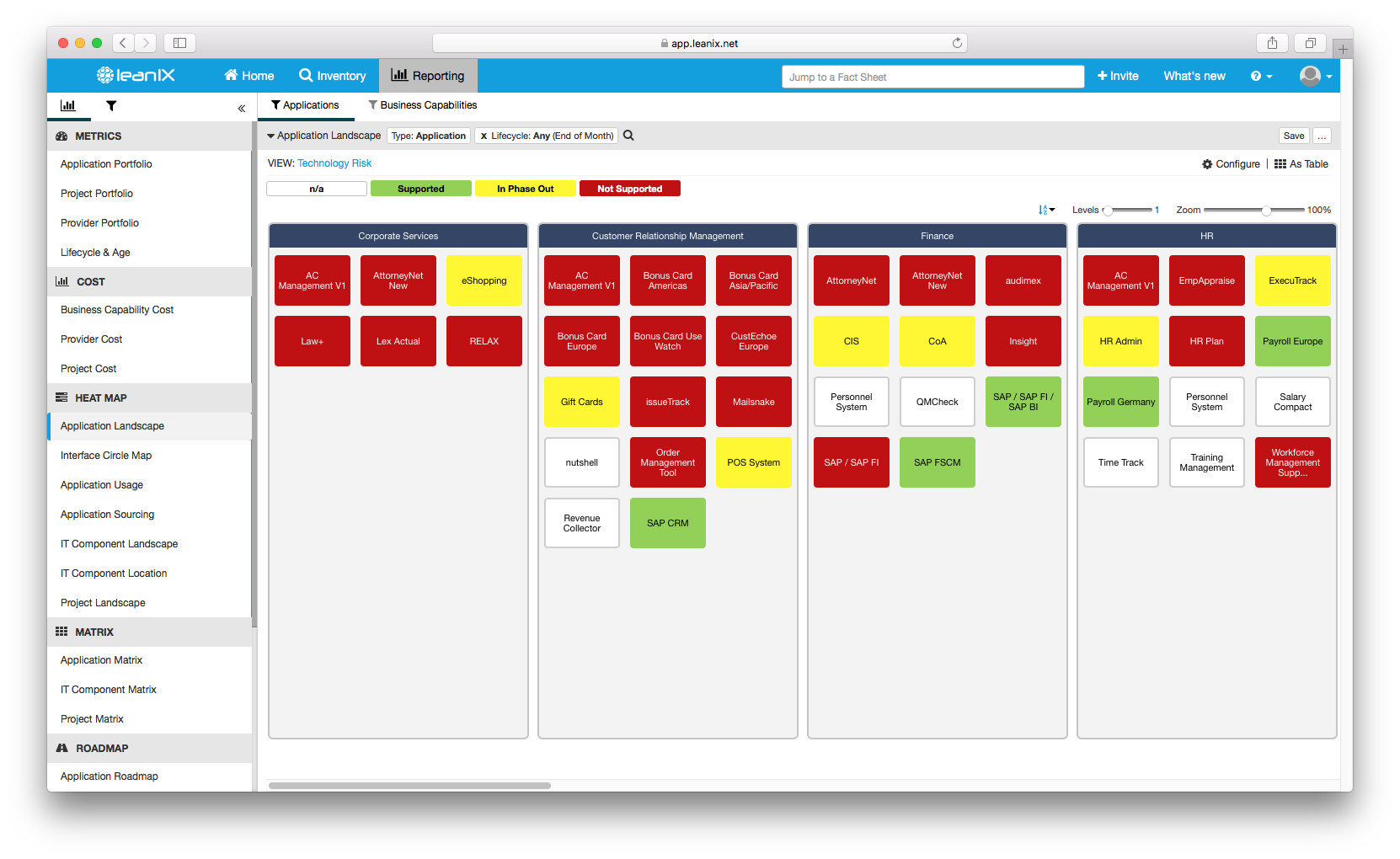
Image 2: Application Landscape heat map showing the IT components that the application is built on are not supported anymore
With the help of EA and the use of a collaborative and lean tool like LeanIX, companies can improve the data security by ensuring updates and patches are implemented proactively.
ENTERPRISE ARCHITECTURE & RISK MANAGEMENT:
Okay, we know that EA can improve data security when implemented in the security planning process, but what about existing security flaws?
100% full security can never be guaranteed. A steadily growing IT landscape, which is without any security flaw, would require a business to run an endless amount of time, resources and money. A better approach for organizations is to commit themselves to mitigate and manage risk to the best of their abilities.
Consequently, EA plays an integral part in risk management, too. As a matter of fact, EA is more widely appreciated for its risk management applications than its role in security. A well-organized EA for Risk management is the foundation of how EA for implementing security works.
The comprehensive assessment of business assets (i.e., technology and humans) by Enterprise Architecture indicates that EA is best capable of aligning security and risk management with business goals and objectives. It helps an organization to allocate time and money better to improve security, as well as the resources available to do so. One reason, therefore, is the objective view enterprise architecture analysis provides for an organization.
To better understand this, here is an example of everyday life.
Consider the risk of traveling. The fear of flying is more common than the fear of driving in a car. For the organization, this could mean to spend more resources on mitigating the risks of flying. However, an objective Enterprise Architecture analysis would uncover, that despite fear, the risk of traveling by car is much greater.
Applying the same logic to security spending, Enterprise Architecture analysis would give the company a suggestion of how to prioritize security improvements. For example, a survey can help to rate data protection risk and to identify security issues (i.e. how well does my Application portfolio adhere to security standards?)
The Survey feature of LeanIX provides the initial answers as a starting point for defining useful security checks and appropriate measures. The survey allows you to query and identify deficits in your IT landscape. The responsible owner can provide possible recommendations for preventative measures via the comment field in the Survey feature.
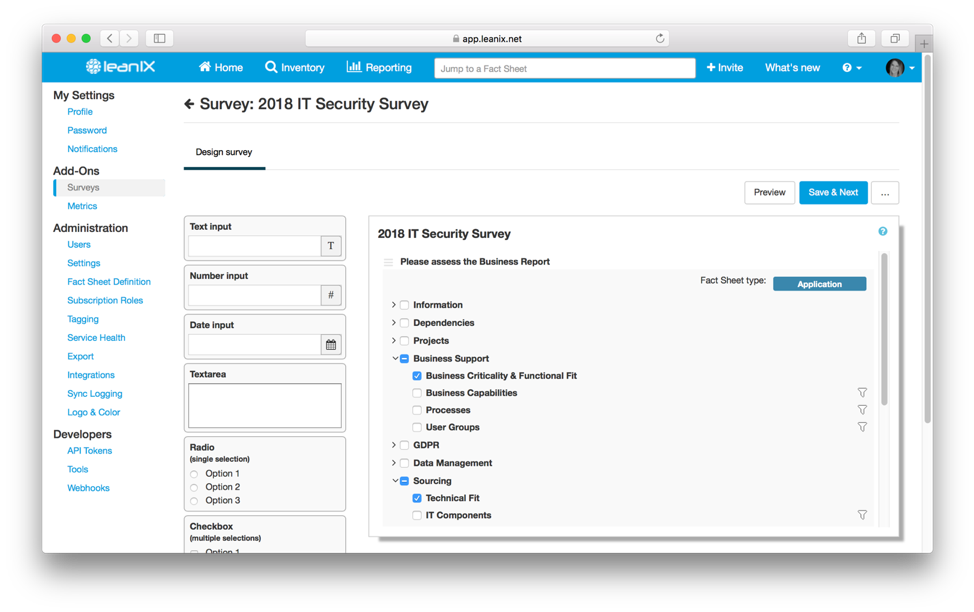
Image 4: LeanIX´ Survey showing how to efficiently do an IT-security assessment.
Case study: Learn how McKesson uses Enterprise Architecture to demonstrate GDPR compliance
Andreas Bosch, Enterprise Architect for leading health wholesale and retail company McKesson, gave an in-depth speech at EA Connect Day on how McKesson uses LeanIX to demonstrate GDPR compliance. McKesson was founded in 1835 and services 2 million customers daily in 13 countries across Europe. With about 600 employees in IT, McKesson Corporation is #5 on the Fortune 500 and delivers 1/3rd of all prescriptions in North America. As McKesson Corporation has US $199 billion in combined revenue in the last fiscal year, they have a lot to lose - upwards of $4 billion.

![Nine Use Cases Solved With Enterprise Architecture [White Paper]: Find out where Enterprise Architects add value and learn how to address post merger harmonization, change from monolith to microservices, IT technology risk, data compliance, integration architectures and more. »](https://no-cache.hubspot.com/cta/default/2570476/9200acfc-8a43-4e3c-9bf0-cd2be30b5346.png)
![Enterprise Architecture Success Kit [White Paper in EN]: Hilfreiche Ideen des LeanIX Teams, wie Sie Enterprise Architecture in Ihrem Unternehmen etablieren. »](https://no-cache.hubspot.com/cta/default/2570476/2e9062c9-9af3-4c91-bdda-69d03157b88c.png)

/EN/Reports/Thumbnail-Obsolescence-Gartner.png?width=140&height=100&name=Thumbnail-Obsolescence-Gartner.png)
/EN/White-Paper/EN-IDC-Inforbrief-Application-Rationalization-Portfolio-Management-Thumbnail_v2.png?width=140&height=99&name=EN-IDC-Inforbrief-Application-Rationalization-Portfolio-Management-Thumbnail_v2.png)